- Use Stack Protector All (stack Canaries For Macbook Pro
- Use Stack Protector All (stack Canaries For Mac Os
- Use Stack Protector All (stack Canaries For Macs
I was looking for a way to enable stack canaries for my ios application in swift but then i found that recent version of xcodes have the flag required to enable stack canaries is enabled by default. So then i was looking for a way to ensure the stack canaries are enabled and as the other sites say i tried with the otool command in terminal($ otool -Iv appName |grep stack_chk) to ensure it and expecting it to return 'stack_chk_guard and stack_chk_fail' flags but it did not return any value/flags. So I then tried setting manually the flag '-fstack-protector-all' under 'other C flags', still I could see no flags with otool command
Writing bug-free software is hard
Writing “good” software, for whatever definition of good you pick, is not easy.It can be even more difficult to write software which is secure. There area number of techniques available for helping one develop software whichhas few or no security vulnerabilities. Examples include creating an architectureinformed by potential threats to secure development practices. No techniqueis perfect, but when combined together the expectation is that the resultingproduct should have fewer vulnerabilities, and those that exist should havereduced impact if found.
Add a better heuristic to use with this than -fstack-protector-all ('can corrupt memory' - canary) support leaving SelectionDAG SSP enabled for sibling call optimization compatibility The AArch64 implementation is far from ideal performance-wise, since it depends on forcing the generation of a proper frame to store and load the return address. Fstack-protector: enables stack protection for vulnerable functions that contain buffers larger than 8 bytes. This includes functions that call “alloca”.-fstack-protector-all adds stack protection to all functions.-fstack-protector-strong: like -fstack-protector. But it includes additional functions that have local array definitions,. Fstack-protector enables protection, but only inserts protection for functions that have arrays in local variables -fstack-protector-all Enable protection, insert protection for all functions -fstack-protector-strong -fstack-protector-explicit Only protects functions with explicit stackprotect attribute -fno-stack-protector Disable protection.
Nothing is free, and each technique includes trade-offs. The trade-offs manyrelate to an increased development effort or increased cost to a product.For an embedded system, where devices may have reduced memory or CPUhorsepower, that cost may be reduced performance.
Unless a system is trivial, it contains bugs. Writing software without bugsis hard, and proving that there are no bugs is even harder. As security isan emergent property in a system, demonstrating that a system is free ofvulnerabilities is a difficult problem. One interesting technique foreither reducing the impact of vulnerabilities or stopping them frombeing exploitable is to “harden” a program by instrumenting the resultingbinaries to check for issues at runtime. These issues can be buffer overflows,out-of-bounds object accesses, etc.
Recently I was in a position where I needed to propose and defend theaddition of “hardening” options to a networked embedded product. The goalwas to help find existing and new defects in-house and protect customersfrom being vulnerable to exploits from yet undiscovered defects. One of thehurdles was determining the performance implication of the different hardeningoptions.
This post, as well as several future posts, will each tackle a singletopic on hardening a product. As well as providing details on the topic,some performance metrics will be presented. The expectation is thatthe analysis should give some context to if the protection a hardening optionprovides is worth the performance trade-off.
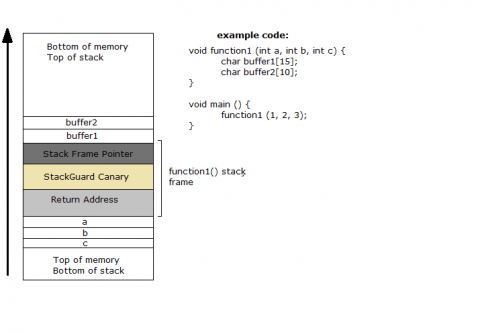
Stack smashing protection
This post’s topic is Stack Smashing Protection (SSP). SSP is a techniquewhere a compiler will instrument a binary to check if part of the program stackhas been overwritten. A canary is placed before the return address on the stack.Before returning from a function the canary is verified. If the value of thecanary matches the original value, the function returns. Otherwise, somethingchanged the value of the canary (which could be a buffer overflow, and out ofbounds write, etc) and the program is terminated. As a result, a potentialexploit is reduced to a denial-of-service.
First, how does SSP work? I’ll speak to GCC’s implementation of SSP; other compiler’s implementation are likely not too different.
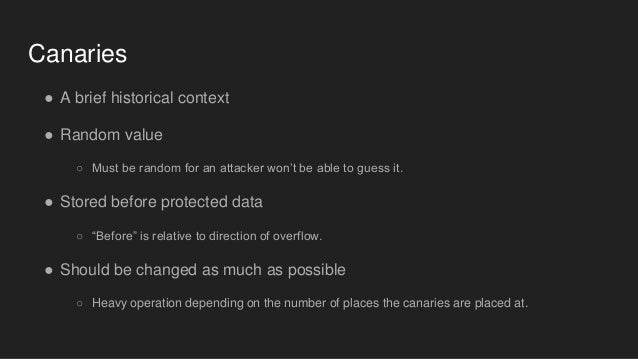
When a program first loads, a stack canary is determined which will be usedfor the rest of the program’s run. GCC’s implementation in libssp can be found here.On Linux, the canary is read from /dev/urandom; if the read value is ‘0’an alternative value is used.
During execution if a function is instrumented it will write the canaryon entry and check it before returning. If the canary does not match,the program is terminated. Following is an example of how the instrumentedcode may look [source]:
Terminating the program is not straight forward, unfortunately, as the stateof the program is not known when a failure is detected. For example, raising asignal may not work, as signals may be blocked. When terminating a program,libssp will make multiple attempts to stop the program.
Not all functions need be instrumented. GCC provides three options [details here]:
-fstack-protector:Functions with vulnerable objects, which include buffers larger than 8 bytesor calls to alloca, are instrumented.
-fstack-protector-strong:In addition to the functions instrumented by -fstack-protector, this flag alsoinstruments functions with local arrays or references to local frame addresses.
-fstack-protector-all:Every function is instrumented.
Instrumenting all functions is known to result in a significant performance hit [source].-fstack-protector and -fstack-protector-strong attempt to mitigate this byinstrumenting only a subset of functions. Traditional stack overflows are theresult of string-based manipulations, and -fstack-protector is intended tocover many of these cases. However, there are rare cases where stack overflowsare caused by other types of stack variables. -fstack-protector-strong is intendedto cover more of these cases [source].
Use Stack Protector All (stack Canaries For Macbook Pro
Analyzing stack smashing protection
As -fstack-protector-strong strikes a balance between security and performance,this version of SSP is analyzed. Two metrics relevant to an embedded system willbe used for the analysis:
- Increased code size
- Performance cost
To facilitate the analysis, a custom Linux distribution was built using Yocto,one build with SSP enabled and one without. The build was run on QEMUand analyzed. See this post onhow to create a custom QEMU image, in my case on macOS.
The Yocto build was a bare-bones build with one exception: FFmpeg was includedwhich will be used to compare performance. Adding FFmpeg was accomplished byadding the following to the conf/local.conf file in the build directory:
To enable SSP the following was added to the conf/local.conf file:
Code size
The Yocto builds were configured to produce a EXT4 file system image.Following are the number of KB used on the file systems:
| Build | Size (KB) |
|---|---|
| No Flags | 34,844 |
| SSP | 35,056 |
This shows that SSP code instrumentation adds an additional 212 KB (~0.25MB)of storage, which is an increase of ~0.6%. Your mileage may vary, as the increasedepends on the type of code being compiled.
Performance cost
Adding the additional instructions will result in some performance cost,as the additional instruction do take a non-zero amount of time to execute.However, the question is can the performance cost be measured or is itexceedingly small?
Use Stack Protector All (stack Canaries For Mac Os
To quantify the performance impact, an experiment was conducted which encodeda small video using FFmpeg. This experiment was selected because video encodingis a non-trivial process and should have a variety of types of code involvedfor encoding, which should provide a use case representative to code usedin real systems. In addition, using FFmpeg itself is a good example to showthe relevance of security, as there have been security vulnerabilities identifiedin the past which could be exploited to execute arbitrary code.(Examples:CVE-2016-10190,CVE-2016-10191,CVE-2016-10192)
The FFmpeg experiment consists of re-encoding a x264 video file in a flvcontainer to a mp4 container as well as re-encoding its aac audio track.The video file is the 640x360 1MB flv file from samples-videos.com:big_buck_bunny_360p_1mb.flv[alternate link].The FFmpeg command line to perform the conversion is:
The experiment took place in QEMU running on a 2015 Macbook Pro, whereQEMU was given 1 CPU and 1GB of RAM. The video file was re-encoded20 times for each build and the processing times were recorded. The laptop wasotherwise idle during the trials to reduce noise in the data. The followingtwo box plots show the resultsof the experiment (raw data here).
Use Stack Protector All (stack Canaries For Macs
The results show that there may be a performance impact when enablingSSP, however if it exists it is modest. The median values of the two plotsare very close, which indicates that both builds can produce encoding timeswhich are similar. Although the first and third quartile of the SSP build areslightly skewed, note that there are also two outliers. These outliers are thefirst two encoding attempts for the SSP trial. As the experiments are runon QEMU, there may be affects on the host system that are difficult to isolate,such as something processing on the host to which I was not aware. If these twooutliers are removed, the results show much closer encoding times:
Conclusion
Stack Smashing Protection does provide some protection against latent bufferoverflow defects which could be exploitable. Enabling it on a system mayslightly increase the storage size of the executables (0.6% in thiscase). There may be a performance hit, however, it is modest at best. If theextra code storage cost is feasible, it may be worth enabling SSP if there isrisk that the system could process data from the outside world which could beused to trigger an exploit.